IEEE 802.11i
IEEE 802.11i, also known as WPA2, is an amendment to the 802.11 standard specifying security mechanisms for wireless networks. The draft standard was ratified on 24 June, 2004, and supersedes the previous security specification, Wired Equivalent Privacy (WEP), which was shown to have severe security weaknesses. Wi-Fi Protected Access (WPA) had previously been introduced by the Wi-Fi Alliance as an intermediate solution to WEP insecurities. WPA implemented a subset of 802.11i. The Wi-Fi Alliance refers to their approved, interoperable implementation of the full 802.11i as WPA2. 802.11i makes use of the Advanced Encryption Standard (AES) block cipher; WEP and WPA use the RC4 stream cipher.
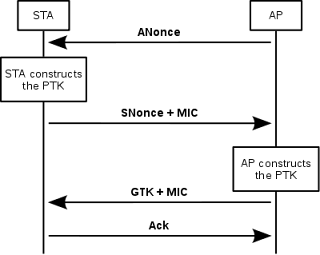
The authentication process leaves two considerations: the access point (AP) still needs to authenticate itself to the client station (STA), and keys to encrypt the traffic need to be derived. The earlier EAP exchange has provided the shared secret key PMK (Pairwise Master Key). This key is however designed to last the entire session and should be exposed as little as possible. Therefore the four-way handshake is used to establish another key called the PTK (Pairwise Transient Key). The PTK is generated by concatenating the following attributes: PMK, AP nonce (ANonce), STA nonce (SNonce), AP MAC address and STA MAC address. The product is then put through a cryptographic hash function.
The handshake also yields the GTK (Group Temporal Key), used to decrypt multicast and broadcast traffic. The actual messages exchanged during the handshake are:
- The AP sends a nonce-value to the STA (ANonce). The client now has all the attributes to construct the PTK.
- The STA sends its own nonce-value (SNonce) to the AP together with a MIC.
- The AP sends the GTK and a sequence number together with another MIC. The sequence number is the sequence number that will be used in the next multicast or broadcast frame, so that the receiving STA can perform basic replay detection.
- The STA sends a confirmation to the AP.
As soon as the PTK is obtained it is divided into three separate keys:
- EAPOL-Key Confirmation Key (KCK) - The key used to compute the MIC for EAPOL-Key packets.
- EAPOL-Key Encryption Key (KEK) - The key used to encrypt the EAPOL-Key packets.
- Temporal Key (TK) - The key used to encrypt the actual wireless traffic.
IEEE 802.11r
The 802.11r standard is designed to speed handoffs between access points or cells in a wireless LAN. 802.11r refines the transition process of a mobile client as it moves between access points. The protocol allows a wireless client to establish a security and QoS state at a new access point before making a transition, which leads to minimal connectivity loss and application disruption. The overall changes to the protocol do not introduce any new security vulnerabilities. This preserves the behavior of current stations and access points.
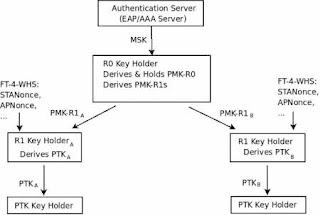
During the initial association in a mobility zone, a 802.11r capable STA and AP perform an Open System Authentication exchange, followed by a a FT Reassociation Exchange that differs from 802.11 Reassociation Exchange by including an MDIE in the Reassociation Request to indicate that the STA wishes to use 802.11r. Moreover, a Fast Transition Information Element (FTIE) is included in the Reassiciation Response frame issued by the AP. The FTIE carries the R0KH-ID as well as the current access point's R1KH-ID. After successful 802.11X authentication, the AP and STA engage in a FT four-way handshake that differs from the 802.11i handshake by carrying extra MDIE and FTIE components, needed for the derivation of PMK-R1s and PTKs.
Exchanges for performing subsequent handoffs within the mobility domain are slightly different. The 802.11r amendment attempts to reduce latency by overlaying key management on top of the 802.11 re association process. The Authentication Exchange and the Association Exchange are used to perform a FT Protocol exchange that allows the STA and AP to agree on the PMK-R1 and derive PTKs. The FT protocol thus replaces the FT four-way handshake and reduces the total number of messages to perform a full re-association to four.
When the STA wishes to (pre-) associate with an AP over the distribution system, the STA and the AP perform an Over the DS FT Protocol exchange. The AP to which the STA is currently associated routes the frames between the STA and the target AP. The FT protocol over the DS uses a new FT Request/Response (Action Frames) Exchange to replace the Authentication exchange followed by an Association Exchange to negotiate cipher suites and derive PTKs on both the STA and the AP.
IEEE 802.11k
802.11k is a proposed standard for how a wireless local area network (WLAN) should perform channel selection, roaming, and transmit power control (TPC) in order to optimize network performance.
802.11k is intended to improve the way traffic is distributed within a network. In a wireless LAN, each device normally connects to the access point (AP) that provides the strongest signal.
Depending on the number and geographic locations of the subscribers, this arrangement can sometimes lead to excessive demand on one AP and underutilization of others, resulting in degradation of overall network performance. In a network conforming to 802.11k, if the AP having the strongest signal is loaded to its full capacity, a wireless device is connected to one of the underutilized APs. Even though the signal may be weaker, the overall throughput is greater because more efficient use is made of the network resources.
The following steps are performed before switching to a new access point.
- Access point determines that client is moving away from it.
- Informs client to prepare to switch to a new access point.
- Client requests list of nearby access points
- Access point gives site report
- Client moves to best access point based on report
IEEE 802.11w
IEEE 802.11w is the Protected Management Frames standard. A key objective is preventing network disruption caused by malicious systems. 802.11w is considering protection to enable data integrity, data origin authenticity, replay protection, and data confidentiality. Support for 802.11w might be implemented by software.
To protect the confidentiality of management traffic, IEEE 802.11w assumes that the client and the access point have exchanged dynamic key content. This precludes the protection of any management frames prior to the delivery of key content, thus exposing network name (SSID) information and other capability information needed for clients to connect to the network. Maintaining backward compatibility for future non-IEEE 802.11w-compliant wireless devices will also be challenging for organizations, limiting the protection afforded by 802.11w until all hardware has been upgraded to support the required functionality.


No comments:
Post a Comment